The NIST 800 Framework - A Brief

Cybersecurity is paramount for organizations across all sectors. The National Institute of Standards and Technology (NIST) has developed a comprehensive series of guidelines and recommendations to help organizations bolster their cybersecurity defenses. The NIST Special Publication 800 (NIST 800) series provides a robust framework that covers various aspects of cybersecurity, risk management, and compliance. This article delves into some key components of some NIST 800 frameworks, highlighting their importance and practical applications.
NIST SP 800-53: Security and Privacy Controls for Federal Information Systems and Organizations

Purpose: NIST SP 800-53 provides a detailed catalog of security and privacy controls designed to protect federal information systems and organizations. These controls are essential for safeguarding operations, assets, and individuals against a myriad of cybersecurity threats.
Key Components
- Control Families: The controls are organized into families, each addressing a specific aspect of security. Examples include Access Control, Incident Response, and Risk Assessment.
- Tailoring Guidance: Organizations can customize the controls based on their specific needs and risk profiles, ensuring a tailored approach to security.
Control Families
1. Access Control (AC): Policies and procedures to regulate who can access information and resources.
2. Audit and Accountability (AU): Mechanisms for tracking and logging access and changes to information systems.
3. Configuration Management (CM): Maintenance of secure configurations to ensure system integrity.
4. Incident Response (IR): Preparation and response strategies for handling security incidents.
5. Risk Assessment (RA): Processes for identifying, evaluating, and mitigating risks.
6. System and Communications Protection (SC): Measures to safeguard information in transit and at rest.
NIST SP 800-37: Risk Management Framework for Information Systems and Organizations

Purpose: NIST SP 800-37 outlines the Risk Management Framework (RMF), a structured approach for managing risks to information systems.
Key Steps
1. Categorize: Define the impact level of the information system based on potential impacts on operations, assets, and individuals.
2. Select: Choose appropriate security controls aligned with the system's categorization.
3. Implement: Deploy the selected security controls and document their implementation.
4. Assess: Evaluate the effectiveness of the security controls.
5. Authorize: Make a risk-based decision to authorize the system for operation.
6. Monitor: Continuously track the security state of the system and make necessary adjustments
NIST SP 800-30: Guide for Conducting Risk Assessments

Purpose: NIST SP 800-30 provides guidance on conducting thorough risk assessments to support effective risk management and information security strategies
Key Elements
- Threat Identification: Recognize potential sources of harm.
- Vulnerability Identification: Identify weaknesses that could be exploited.
- Likelihood Determination: Assess the probability of a threat exploiting a vulnerability.
- Impact Analysis: Estimate the potential consequences of a successful exploit.
- Risk Determination: Calculate the overall level of risk.
NIST SP 800-171: Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations

Purpose: NIST SP 800-171 offers guidelines for protecting controlled unclassified information (CUI) within nonfederal systems.
Key Components
- Basic and Derived Security Requirements: These requirements are divided into 14 families, similar to those in SP 800-53, but tailored for nonfederal systems.
- Implementation Guidance: Practical advice for implementing and assessing the controls.
NIST SP 800-61: Computer Security Incident Handling Guide
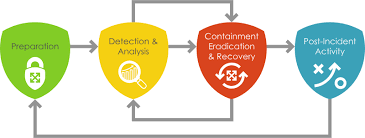
Purpose: NIST SP 800-61 provides a comprehensive approach to incident handling, covering preparation, detection, analysis, containment, eradication, and recovery.
Key Phases
1. Preparation: Establishing and training an incident response capability.
2. Detection and Analysis: Identifying and analyzing security incidents.
3. Containment, Eradication, and Recovery: Responding to and recovering from incidents.
4. Post-Incident Activity: Learning from incidents to enhance future responses.
NIST SP 800-34: Contingency Planning Guide for Federal Information Systems

Purpose: NIST SP 800-34 guides the development and maintenance of effective contingency plans.
Key Phases
- Activation and Notification: Procedures for recognizing a contingency event and initiating the plan.
- Recovery: Steps for restoring operations post-incident.
- Reconstitution: Actions for returning to normal operations and validating system functionality.
Conclusion
The NIST 800 series is an essential resource for organizations seeking to enhance their cybersecurity posture. By following the guidelines and best practices outlined in these publications, organizations can effectively manage risks, protect sensitive information, and ensure compliance with federal requirements. The NIST 800 framework emphasizes a structured, systematic approach to security and risk management, promoting consistency and thoroughness across all organizational operations. Embracing these standards not only strengthens security but also fosters a culture of resilience and proactive risk management.
**Rodgers Munene**
.jpg)


Comments
Post a Comment